Do you run a server that is accessible on the Internet? One of the first steps in securing your server, to prevent unwanted third parties from gaining access, is to disable the root user from logging in via SSH. The article explains how you can no longer permit root login via SSH. The article specifically targets servers running Debian. However, the outlined procedure is similar for other Linux distributions.
Managing an Internet server can be a scary thought. The moment you boot it up, you basically place a big bullseye target on it. People will find its IP address and will try to login via SSH. Some of them have bad intentions and would like nothing more than to wreak all sorts of havoc. Luckily, you can take a few simple steps to secure your server and prevent such unwanted actions from happening to your server. Disabling the root user from logging in, is one of these steps. Keep an eye on this blog in the near future as more security measures for your server will be published.
Here is what hackers will do: They run an automated script to determine if a specific IP address responds, after trying to open an SSH session. Once they found such an IP address, their script repeatedly attempts to login with a common username such as root, admin, pi, etc. combined with all sorts of different passwords with the hope to find the right one. They realize that the moment they manage to login as the root user, they hit the jackpot. At that point they can do whatever they want with your server. As soon as possible after setting up your Debian server, you should change the SSH server configuration to no longer permit root login via SSH.
Before actually doing so, it is important to have another user created on your server, who has rights to run commands as sudo. Running a command as sudo basically gives your user temporary root user privileges, without needing to be the root user. To create a new user with sudo access, login to your server as the root user via SSH and run the following command;
adduser <newusername>
Replace <newusername> with the username of your preference. Just make sure to not pick an obvious one that hackers might guess. Visit an online username generator, if you need inspiration. The command prompts you to enter some basic information about the new user, including the password. The password should be a strong one. You can generate such a password with online tools such as this password generator. Next, run the command to add the new user to the sudo group:
adduser <newusername> sudo
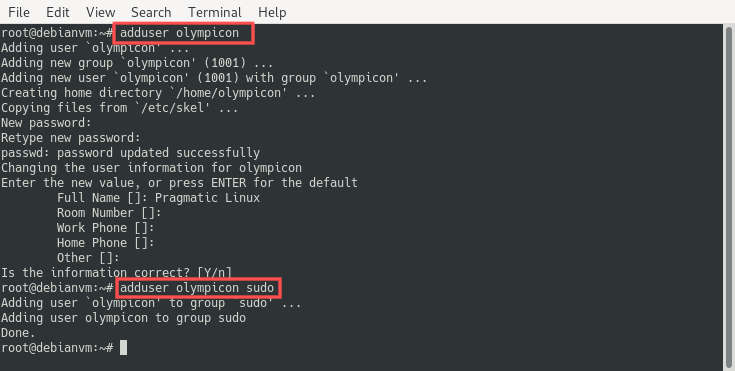
Before access for the root user via SSH is disabled, make sure you can actually login as the newly created user and that you have sudo access. Go ahead and close the SSH session as the root user and login as the new user via SSH (ssh <newusername>@ip-address or ssh <newusername>@hostname). Next, run the following command to test that sudo access is granted:
sudo apt update
Now that you verified the new user, it is time to move on to the important part, where you reconfigure the SSH server to no longer permit root login via SSH. The Nano terminal editor is perfect for changing the SSH server configuration file. Refer to this article for a quick tutorial on editing files with Nano. Run the following command to edit the SSH server configuration file with super user privileges:
sudo nano /etc/ssh/sshd_config
Find the PermitRootLogin variable inside this configuration file and set it to no:
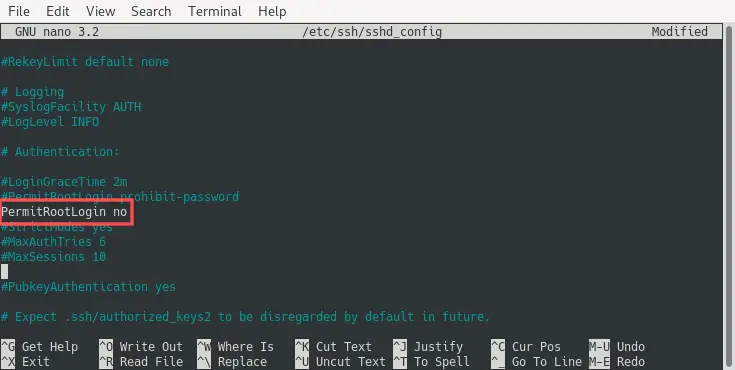
Next, save the changes to the file and exit the Nano editor. As a final step, restart the SSH server to activate the new configuration settings:
sudo service ssh restart
That is it! It is now impossible for the root user to login via SSH. Feel free to go ahead and try it for yourself. A final word of warning: Be careful with which users you give sudo rights. They might change their password to something easier to remember and consequently lower your server’s security.



One thought on “No longer permit root login via SSH”
Comments are closed.